From Cyber Lab you can manage permissions, control devices, update the network configuration and generate reports helping compliance with standards like ISO/IEC 27001 and IEC 62433.
Cyber Lab generates configuration files to our cyber-secure protocol named CBCP. This protocol ensures a cyber secure network configuration. Read further details about CBCP here.
Content:
This page explains how Cyber Lab can be used. We are starting with a simple introduction and then showing more advanced examples at the end. Here is a content list to get an overview.- Simple Introduction
- - Add Hosts
- - Connect to Interfaces
- - Deploy the System
- - Send Commands
- - Search in Device List
- Cyber Lab helps with ISO/IEC compliance
- Add Modules
- Modules for Anything
- Expand the network
- Virtual Office
- Interested to join our Beta-Plus development programme?
Simple Introduction
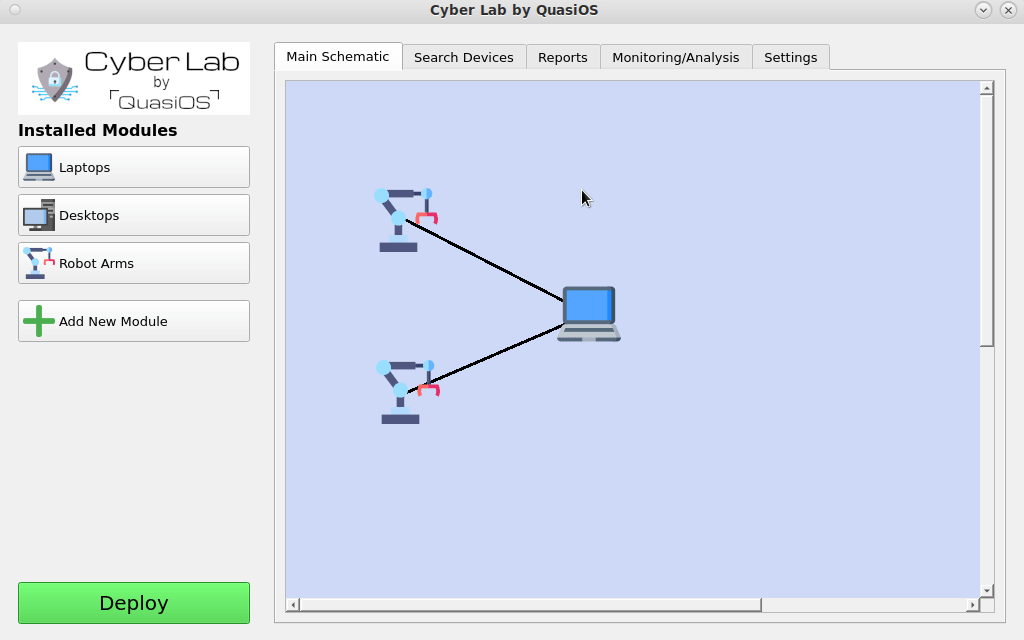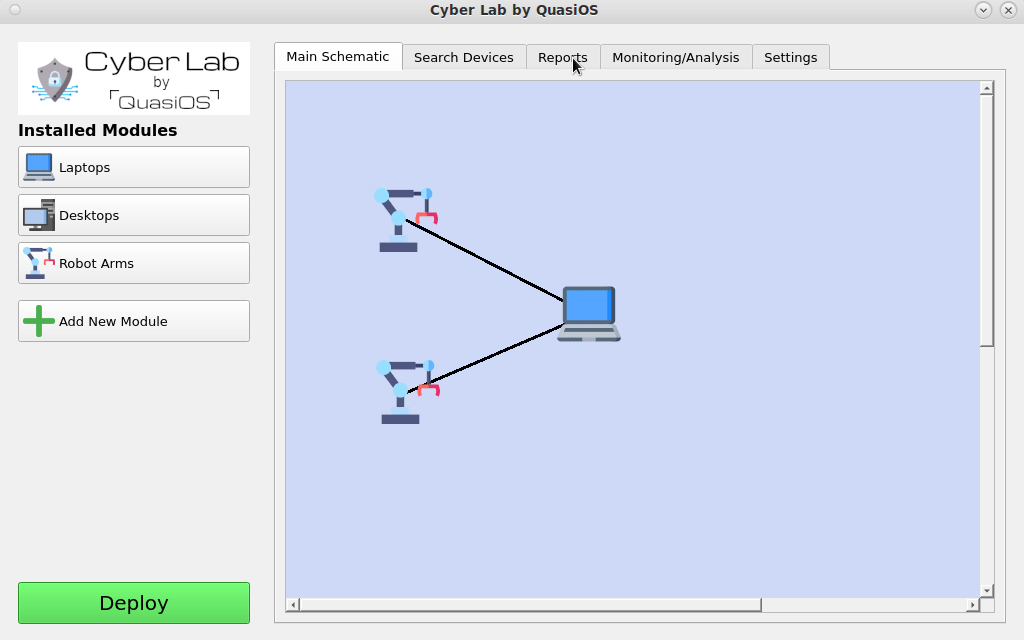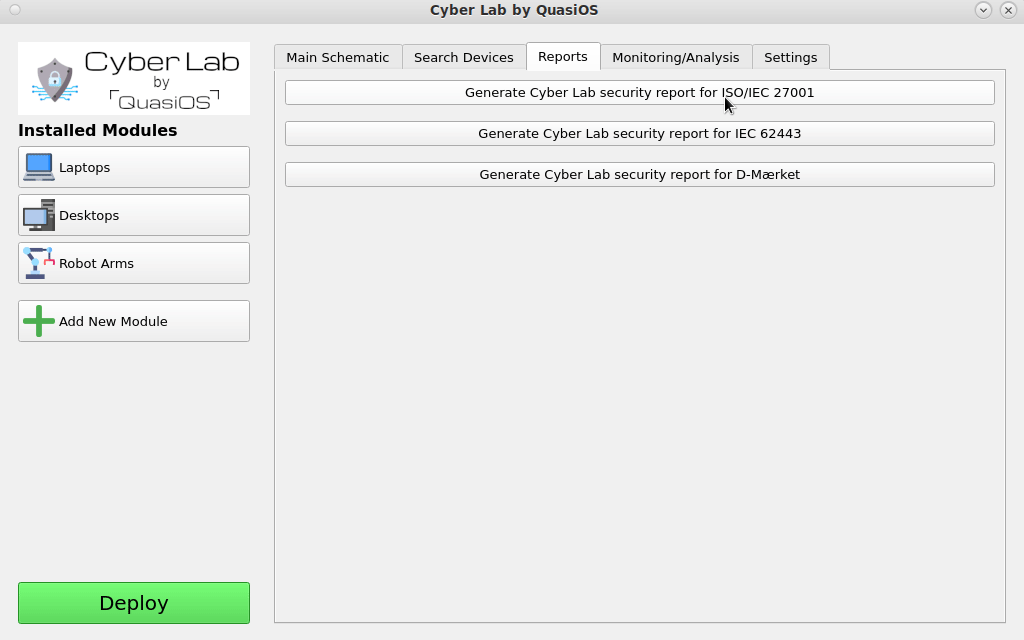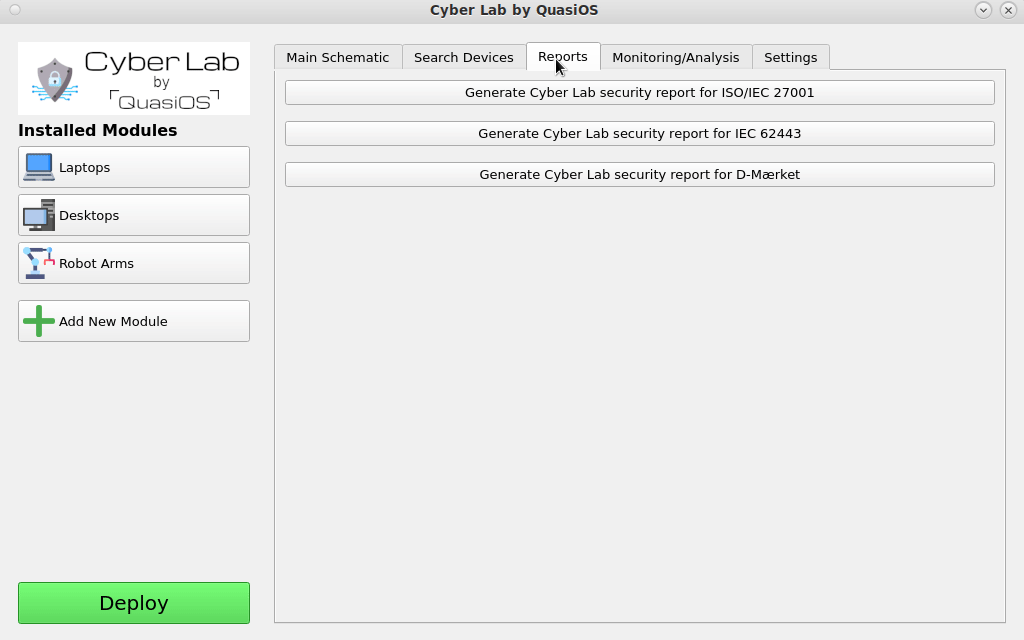
In Cyber Lab we can configure a production facility. In our simple introduction we will consider a setup with a managing laptop and two robot arms.
First the specific robot hardware has to be decided for whatever specification and production needed. When the specification of the facility has been decided we need the specific software vendor modules.
In our example we imagine that we have the facility specification and the vendor software module for the robot arm that has been chosen.
Add Hosts
When we have specified the facility, we are ready to set it up in Cyber Lab. The first thing is to add the hosts we need. Cyber Lab comes with two standard modules for Laptops and Desktops.
For the robot we use the vendor specific module.
We add a host by clicking on the module in the left hand side and type in the information for the host.
Connect to Interfaces
Next we need to define the connections we want. Connect the hosts by selecting the host which should send a command and click on the host you want to send the command to.
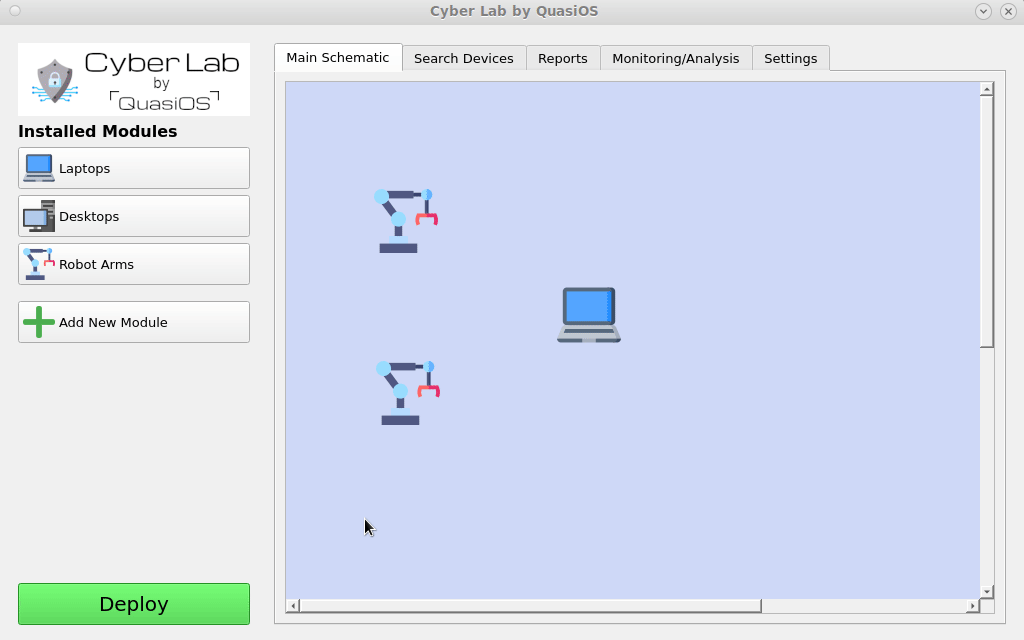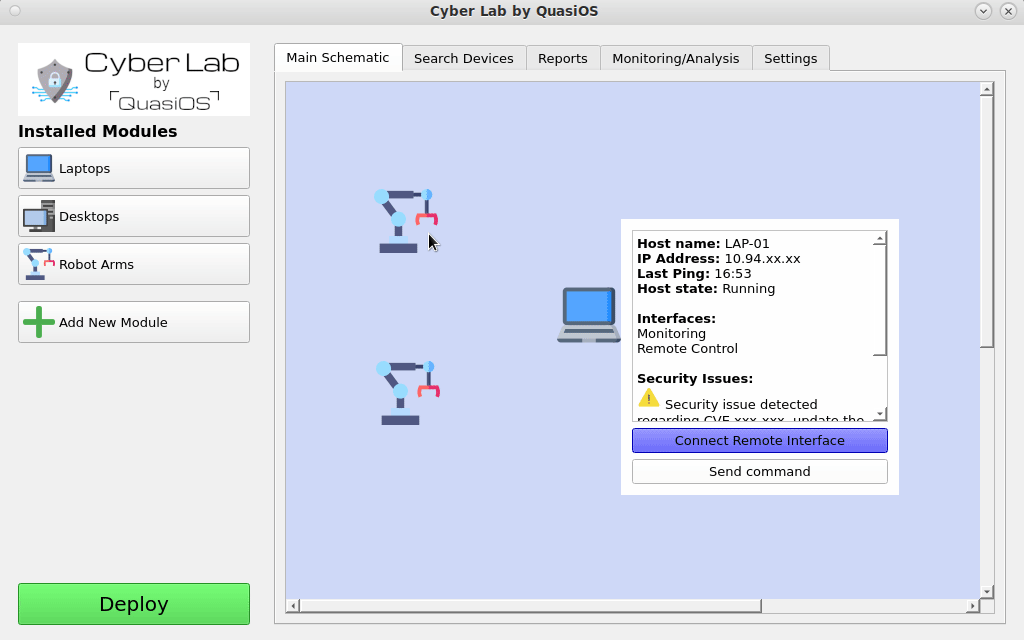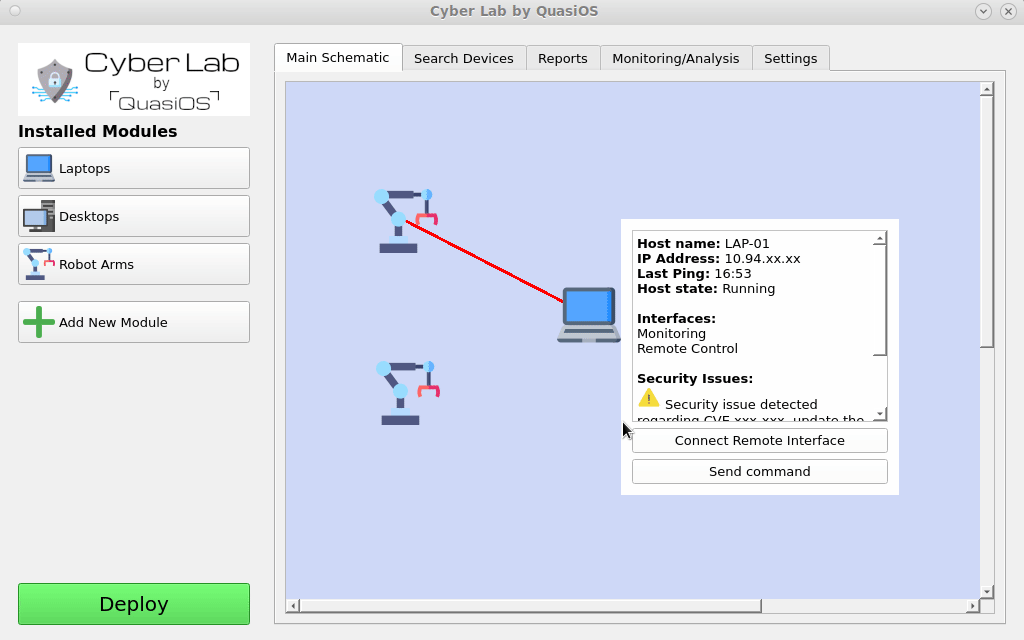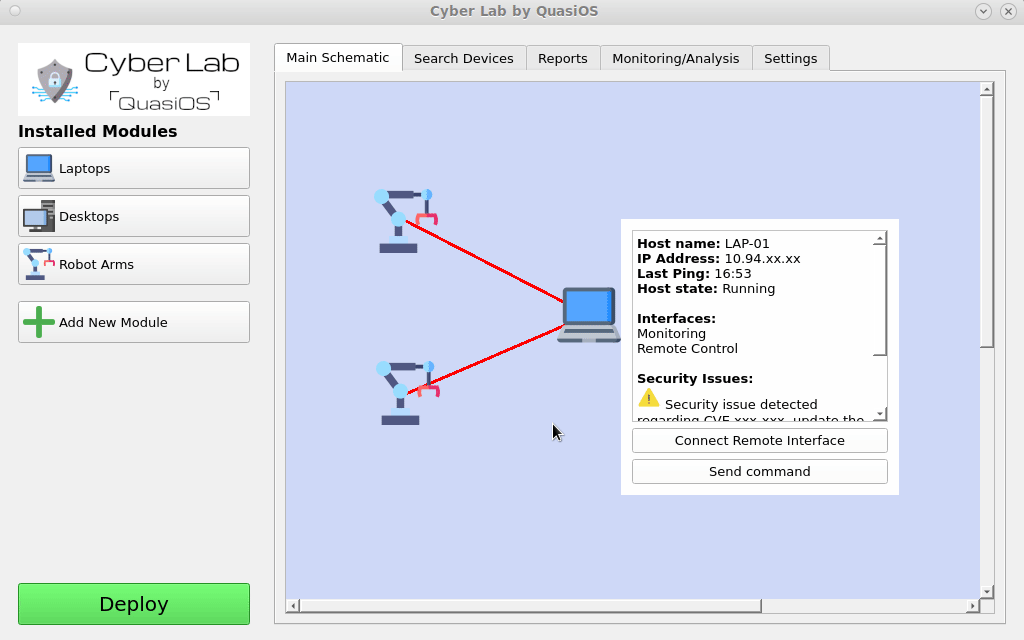
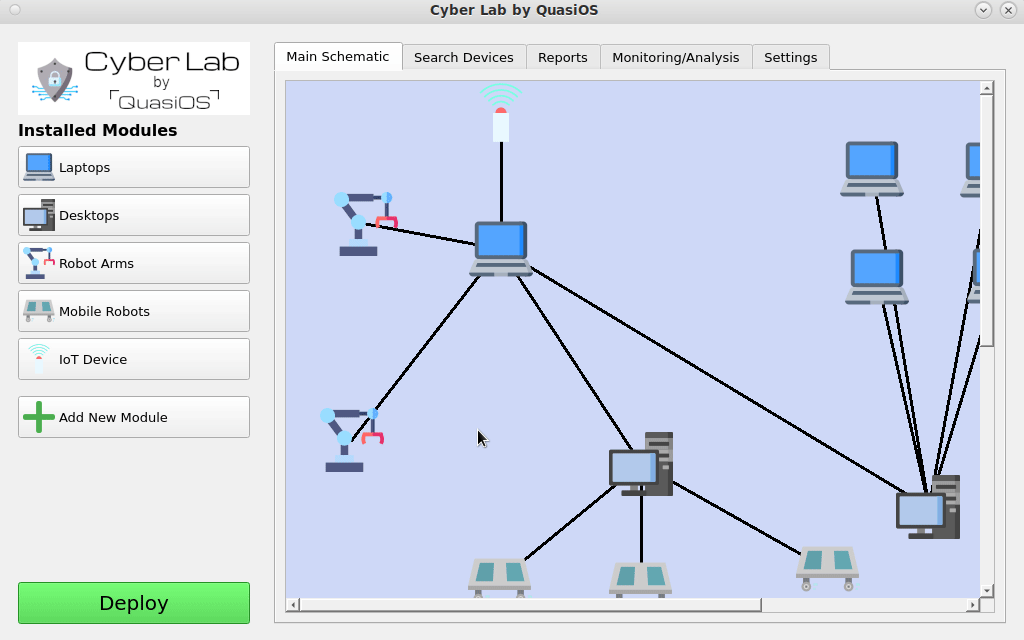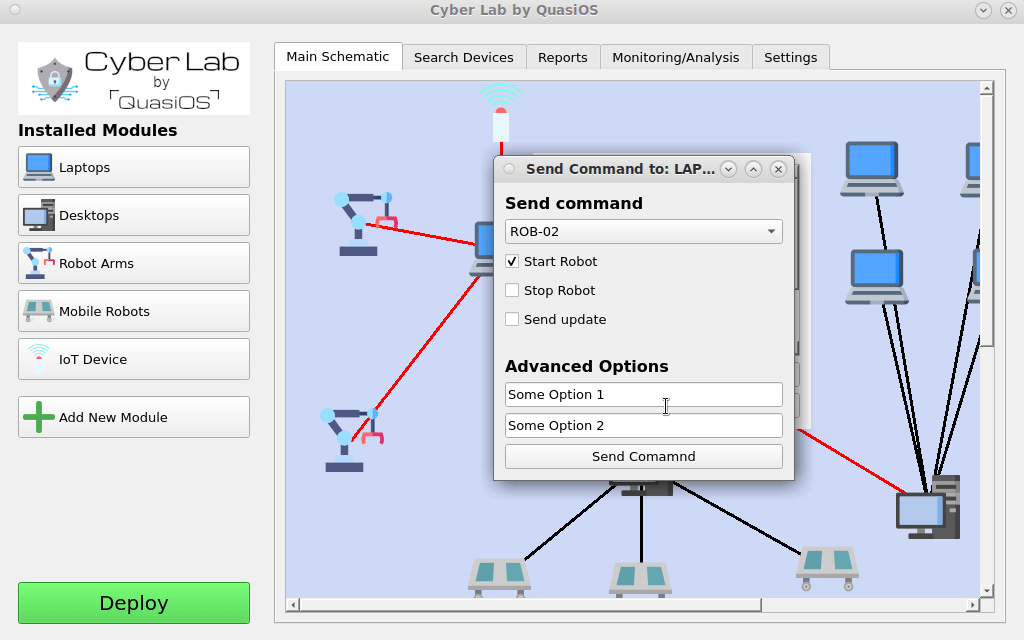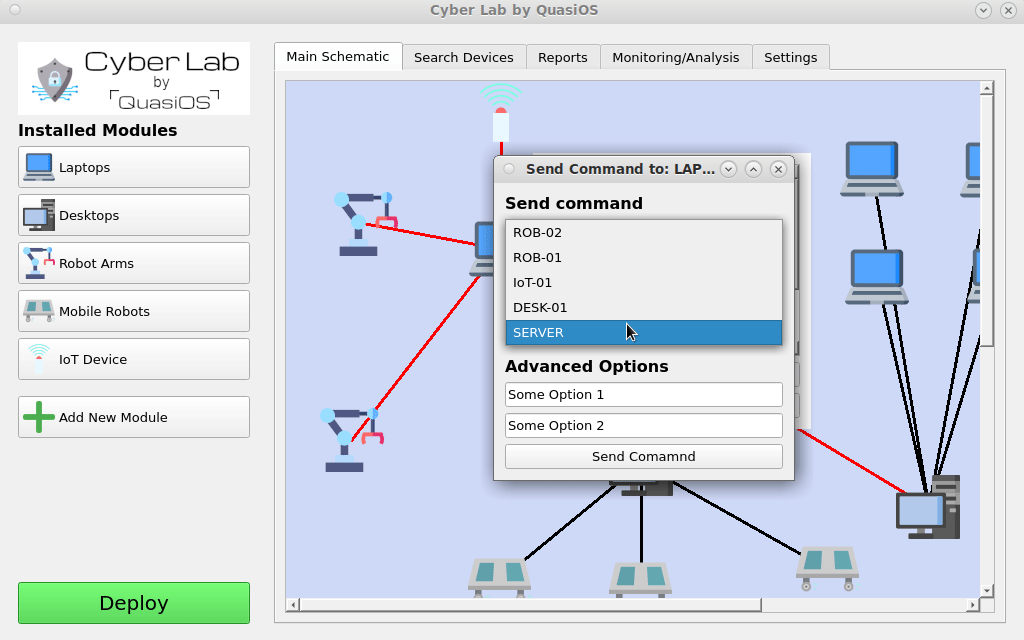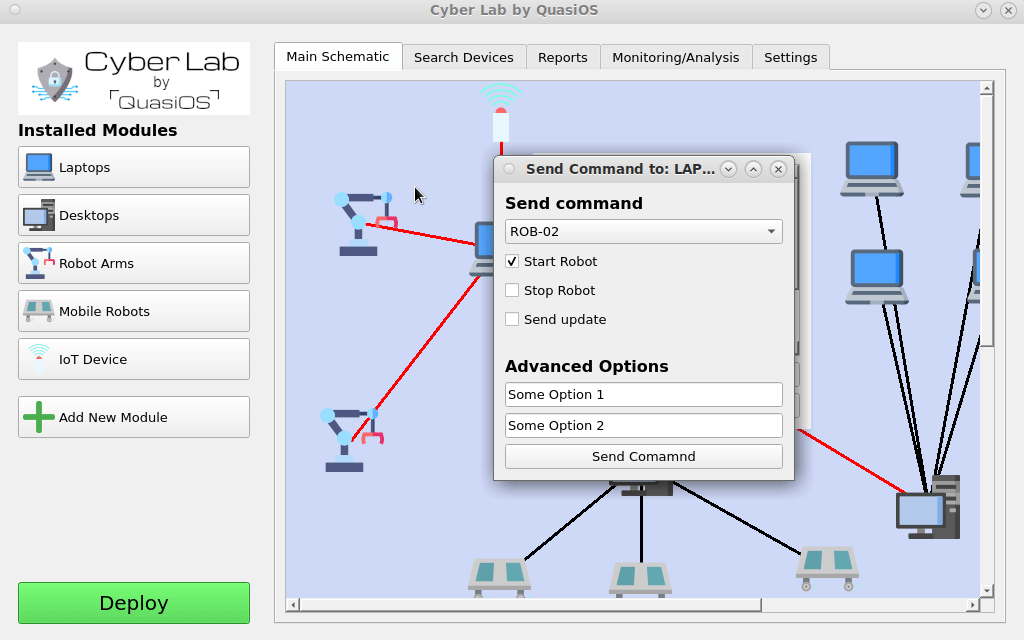
In our case we want the Laptop to be able to send commands to the robot arms via the default vendor interface. The default vendor interface gives us the possibilities to send "start", "stop" and "update" commands.
It is possible to have customized interfaces which gives the possibility to have and define any arbitrary functionality and permissions.
Deploy the system
We are now ready to deploy the system with the specified configuration and permissions. Cyber Lab will generate a cbcp-config file containing the entire setup we have made.
In our example case the cbcp-config file will look as follows: 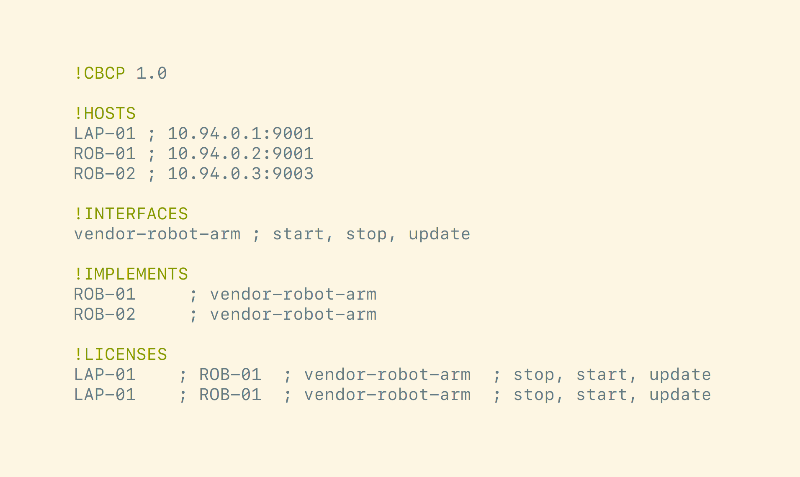
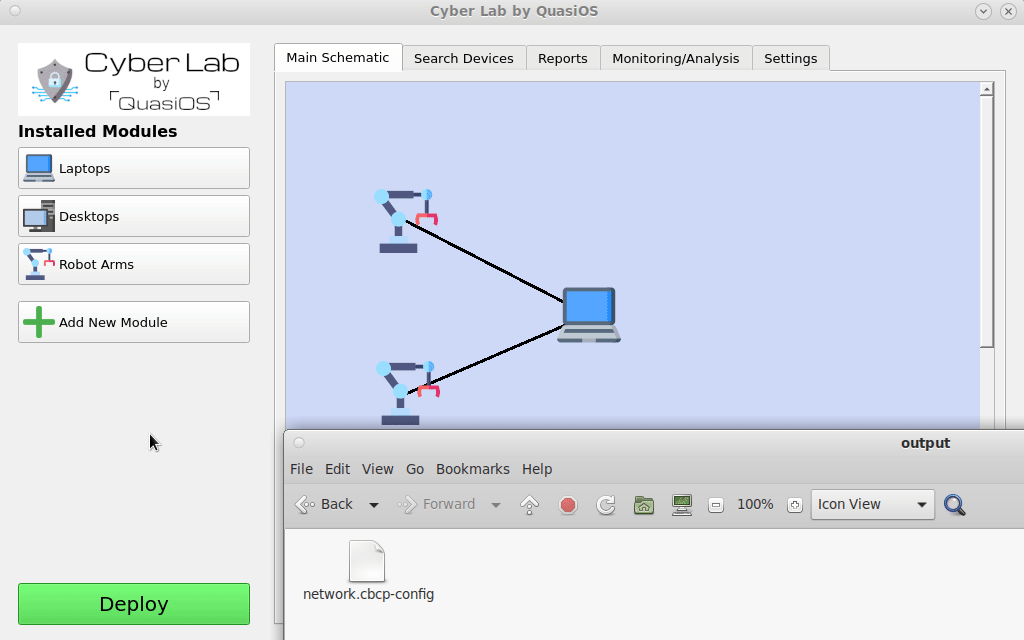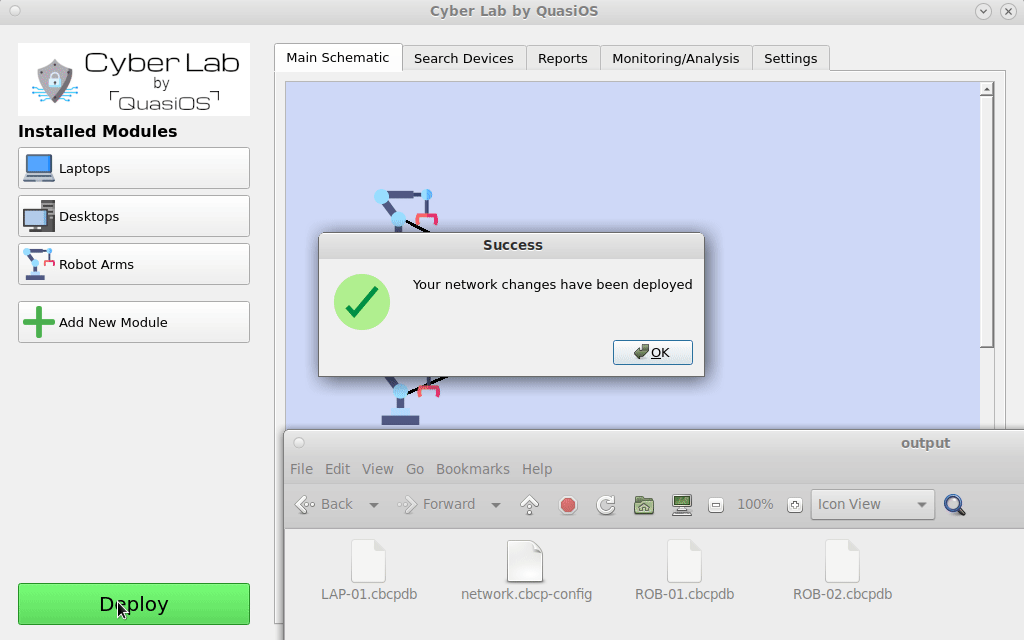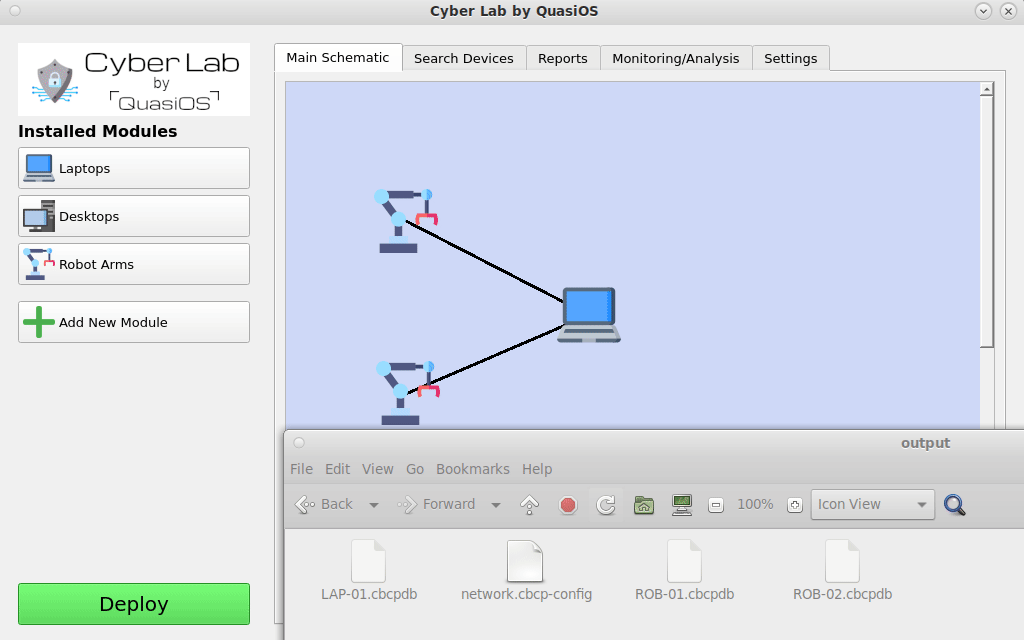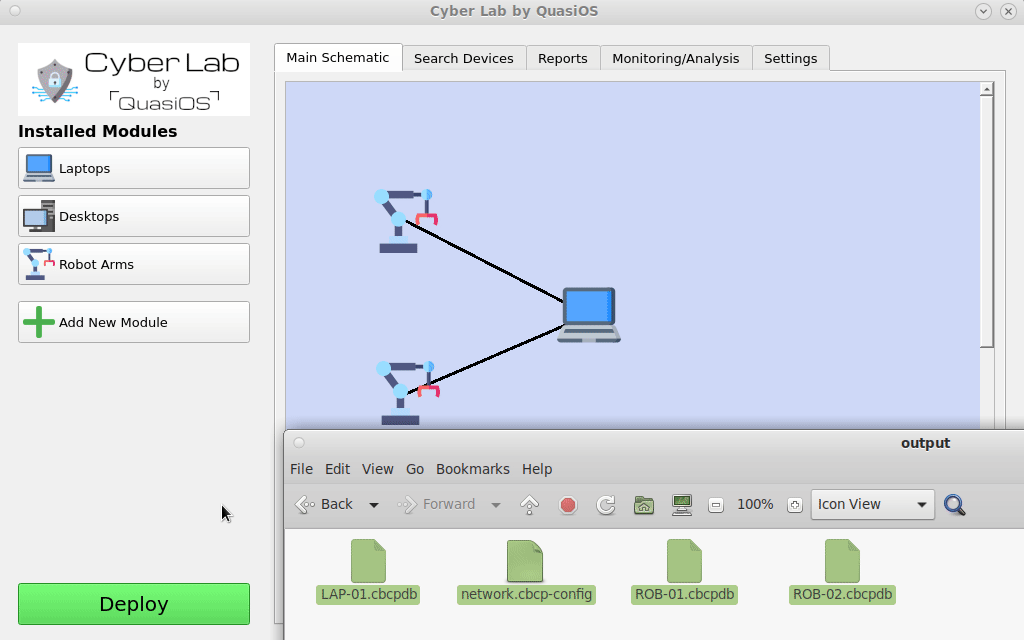
When the "Deploy" button is pushed, Cyber Lab creates cbcp-database files for all devices in the system. At first setup the database files have to be distributed. All hosts must have the database file with its name.
All additional updates to the system can happen completely automatically over the already established CBCP connection, where the updated database files can be sent to the host automatically.
It is important to note that some devices may still require manual updating. For example if it is an embedded device where the chip has to be re-flashed.
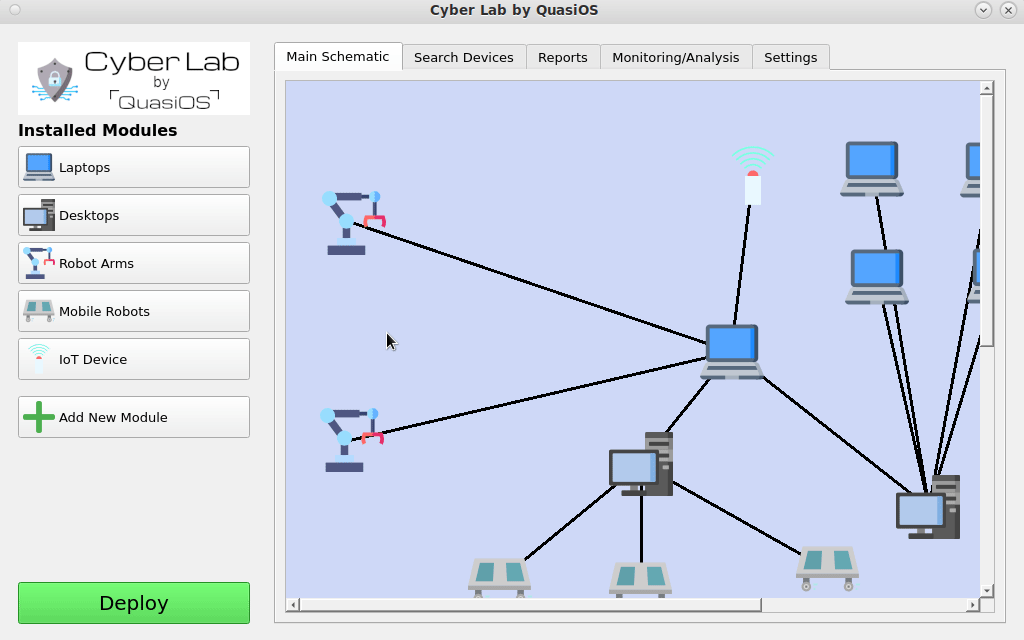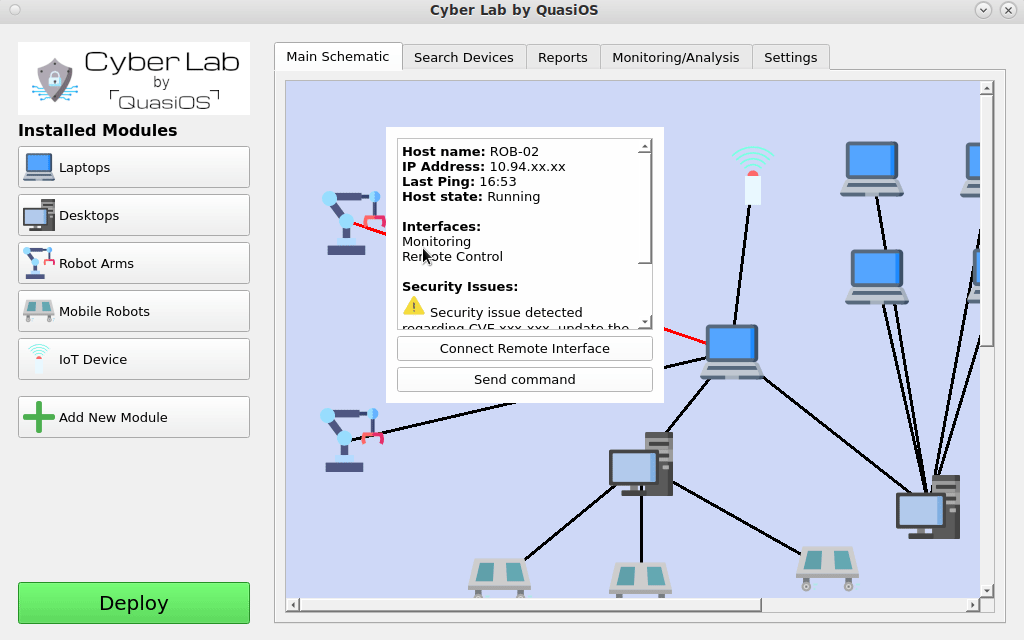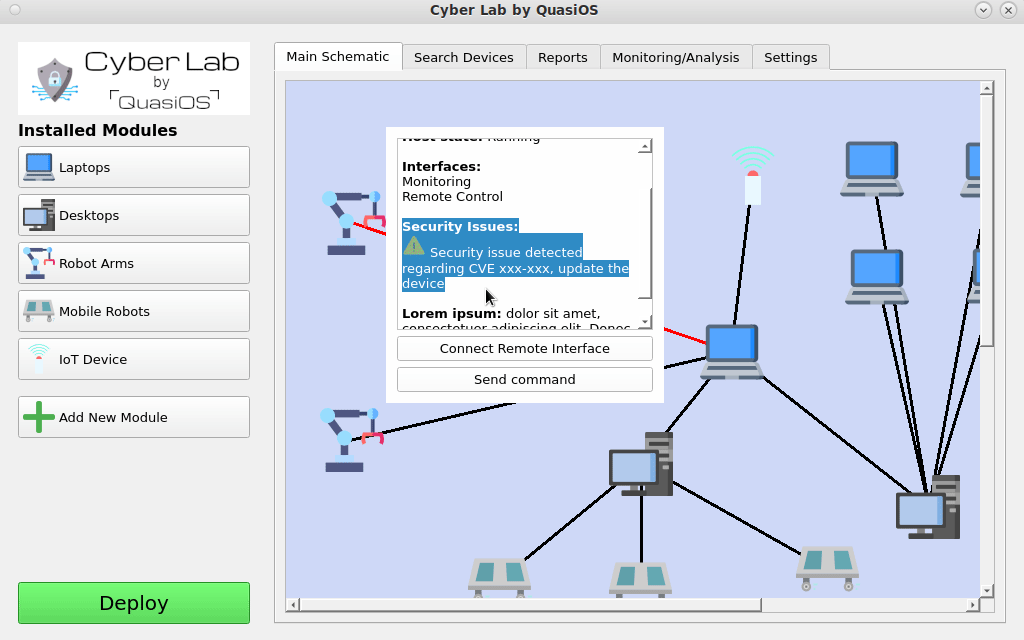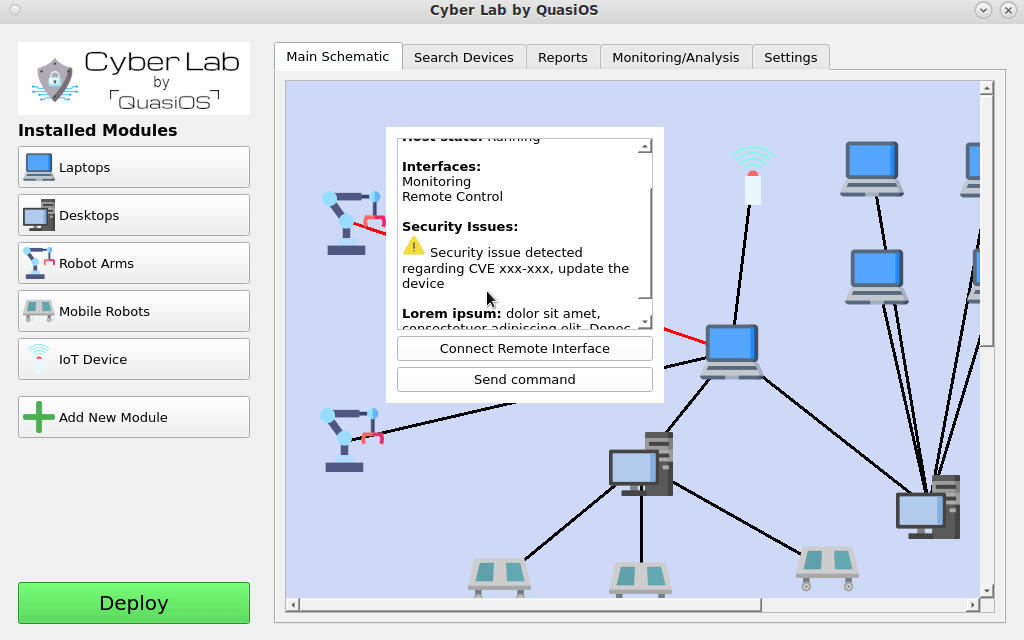
Send commands
When the system has been deployed and all hosts are running, we can start sending commands within Cyber Lab. It is important to note that we can only send the command that we have allowed from the design of our system.
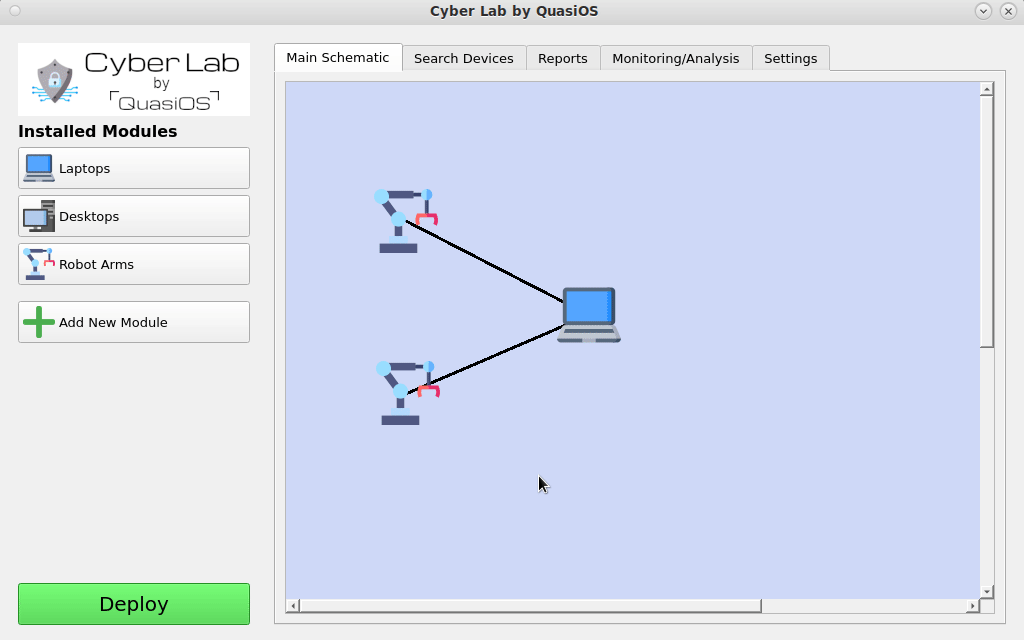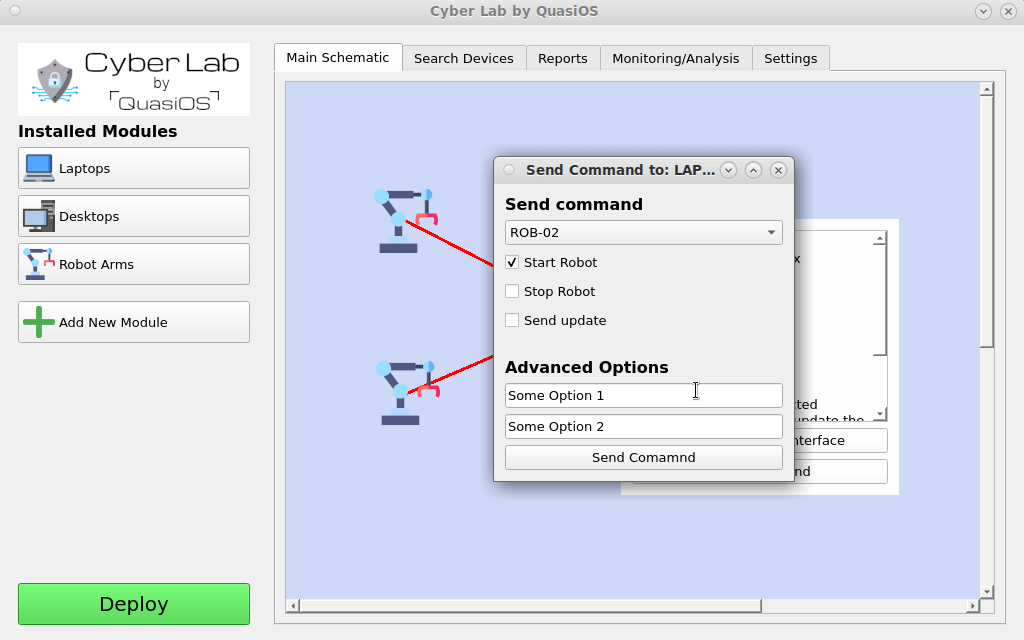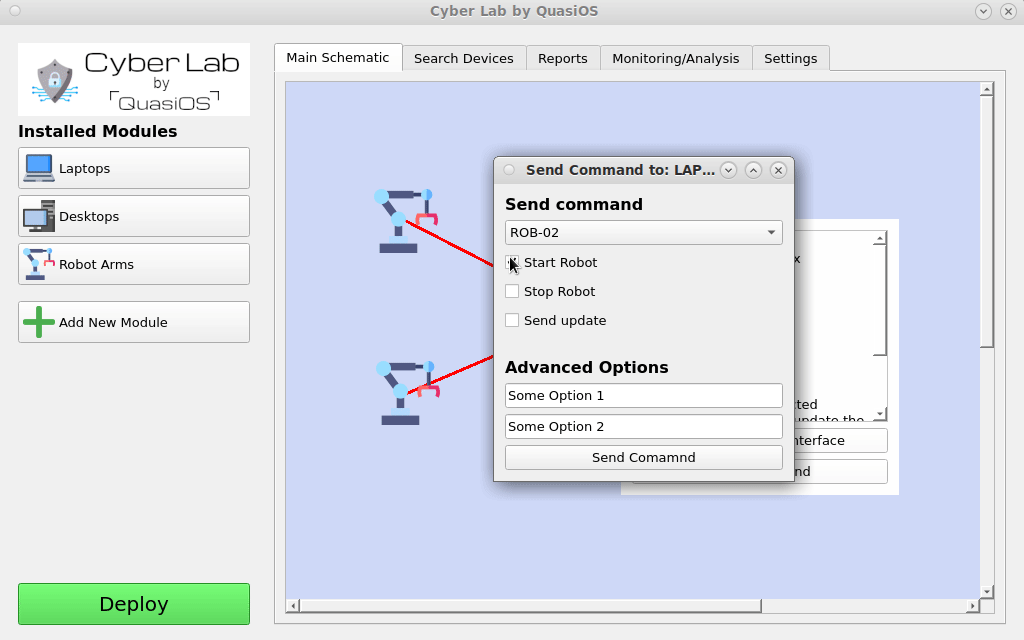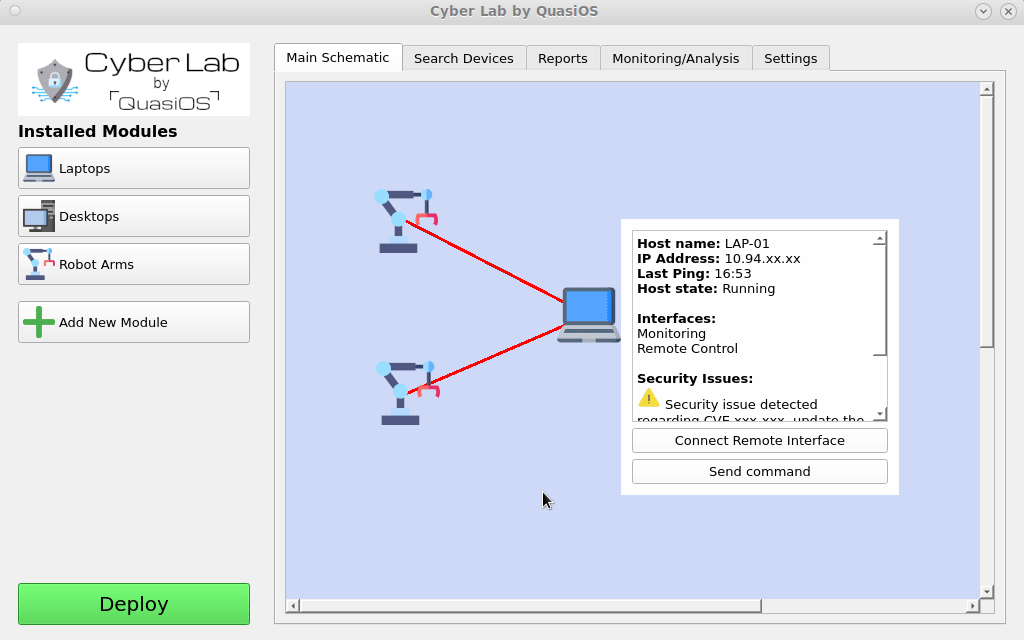
So in our example we are sitting with the Laptop which has Cyber Lab installed. So it is only possible to execute the commands that the Laptop has. So if another laptop is used, the commands would be rejected at the receiving robot.
In Cyber Lab we can select our Laptop and click on the "send command" button. Select the host and command you want to send.
The robot will receive and validate the command, if access is granted, the robot will execute the command.
Search in Device List
Some setups can require a larger number of devices and at some point it might be more convenient to search for a specific device in the device list, rather than find it in the graphical view. Via the "Search Devices"-tab it is possible to get a complete list of all devices in the setup.
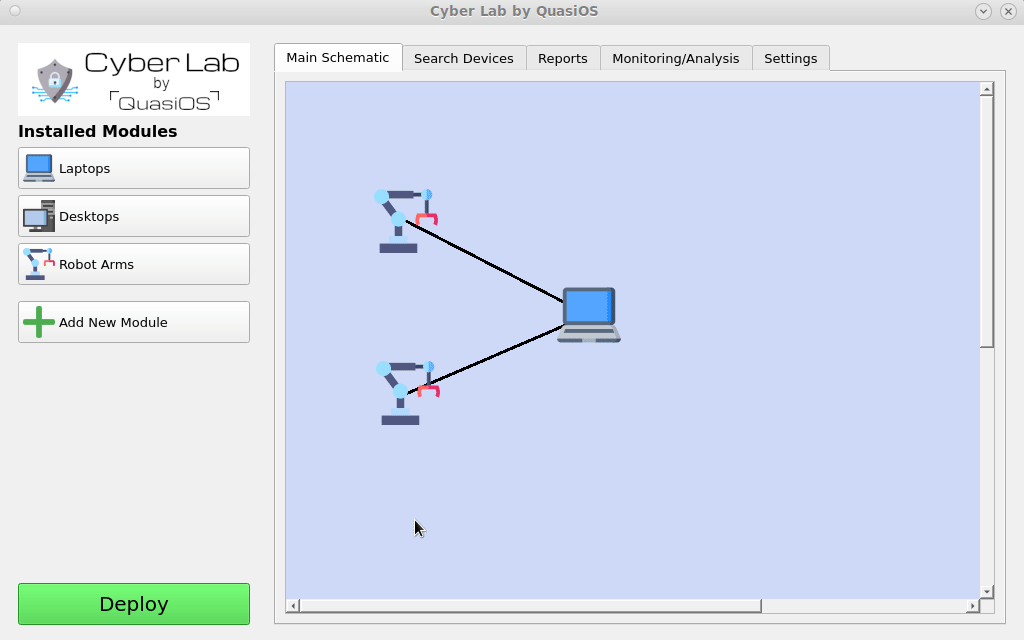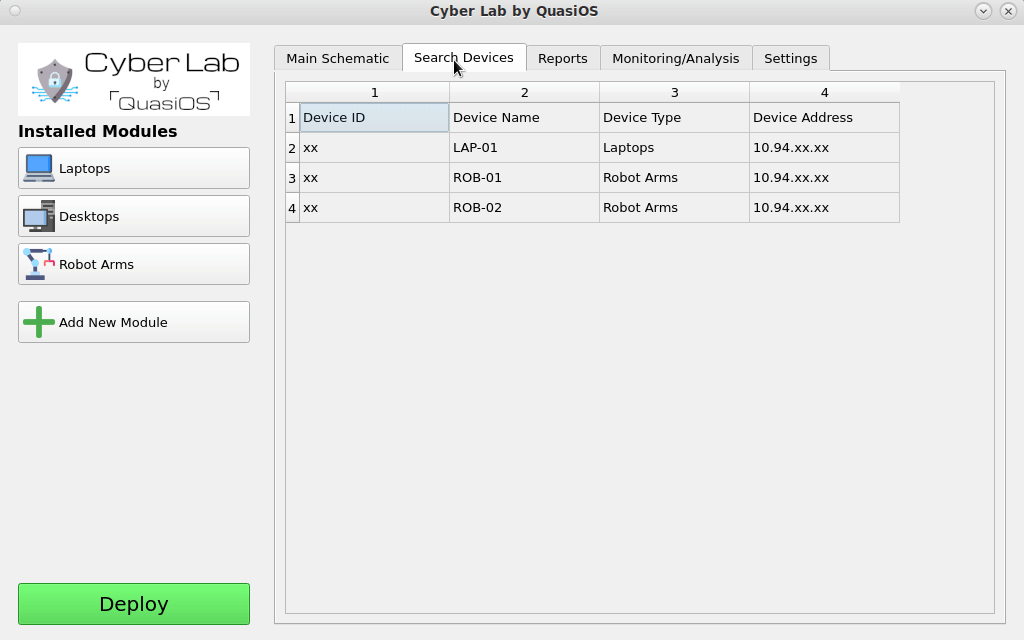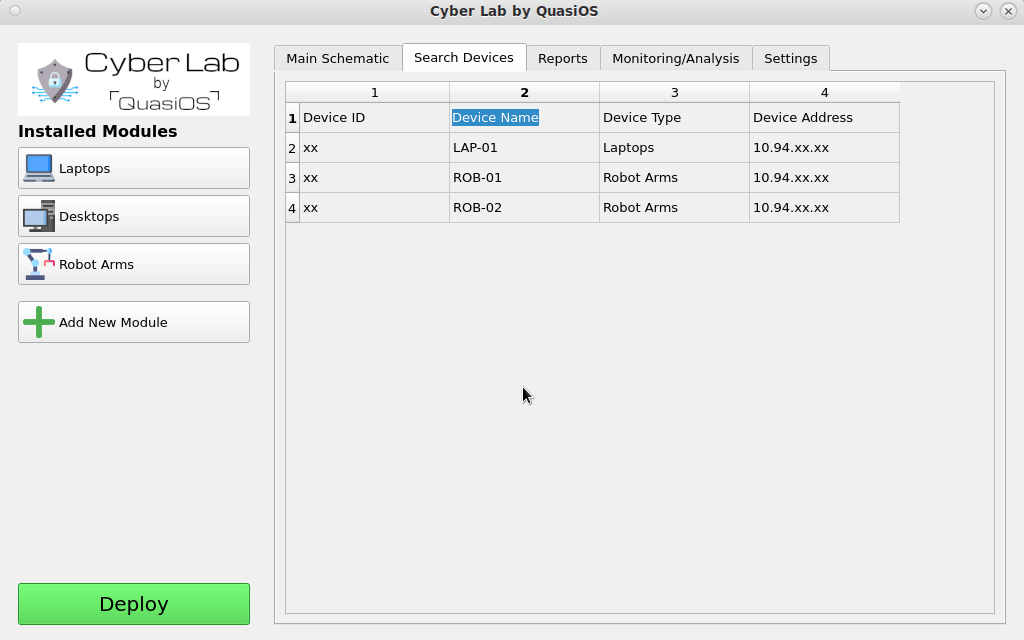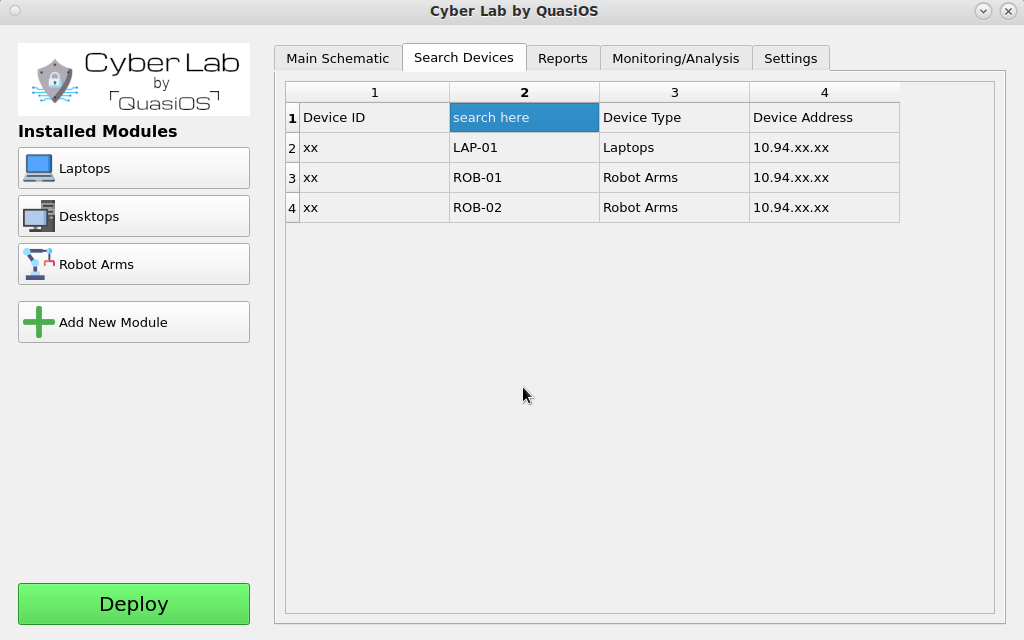
It is possible to search by hostname, host address, filter by device type and more.
Cyber Lab helps with ISO/IEC compliance
With Cyber Lab it is possible to keep track and control a lot of important data and settings. This includes user and system permission, cryptographic keys and data/communication flow.
In standards like ISO/IEC 27001, IEC 62433 and D-Mærket it is required to document some of these details.
This data is nicely stored in Cyber Lab and can be queried. Cyber Lab can produce comparison reports for use in information security risk assessment comparisons.
Concretely Cyber Lab can be used to contribute towards the ISO/IEC 27001 points:
- A.9.2 User access management
- A.9.4 System and application control
- A.10 Cryptography
- A.12.2.1 Control against malware
- A.14.2 Security in development and support processes.
All access permissions are defined when interfaces are connected and the database files are distributed. When the deploy button is pushed the cryptographic keys are generated which are used for all communication defined.
If a policy is made about changing the encryption keys once a month, the deploy button can be used to generate entirely new cryptographic keys for the system.
Furthermore, if system updates go through Cyber Lab, we can keep track of system software version information and inform as shown in the video here, if there should be any known vulnerabilities in the system. This information could both be sent by notification, but also in report format. Our secure protocol prevents malware from propagating through the network. Because we have the system defined in Cyber Lab, it is also possible to easily detect which hosts are physically connected to a compromised host.
Add Modules
When a system is designed some specific hardware is chosen to solve a task. The modules for the specific hardware platforms are needed and can be obtained from the vendor. The modules provide a default vendor interface which gives an off-the-shelf solution to use the specific hardware.
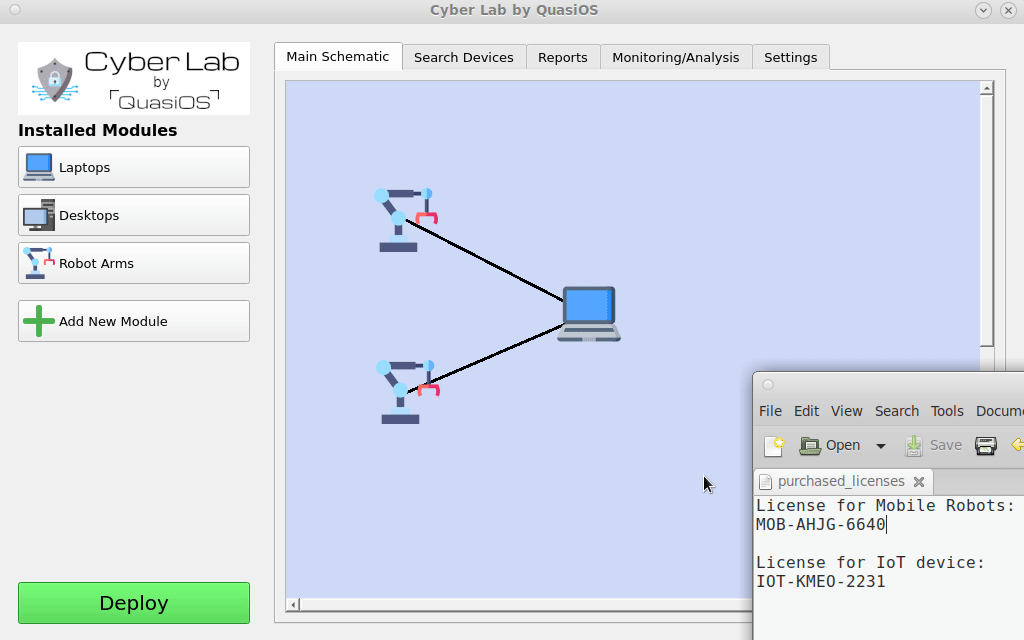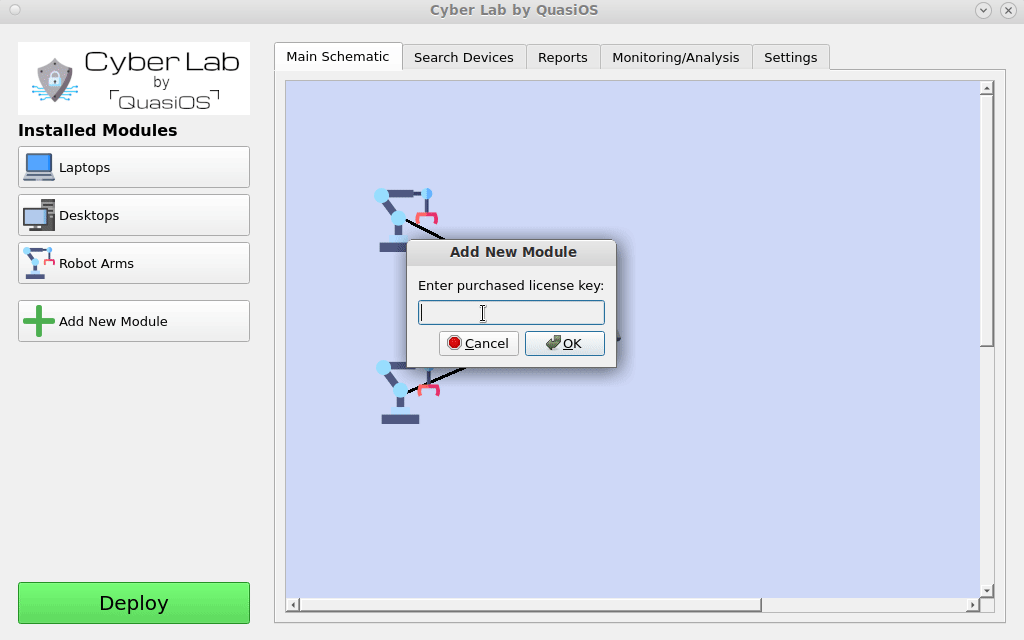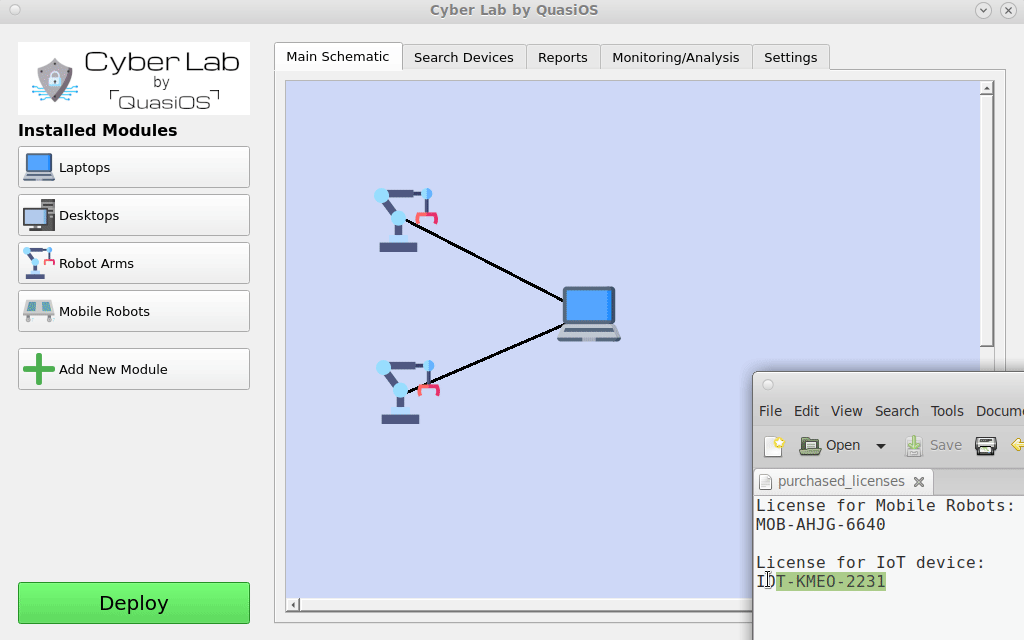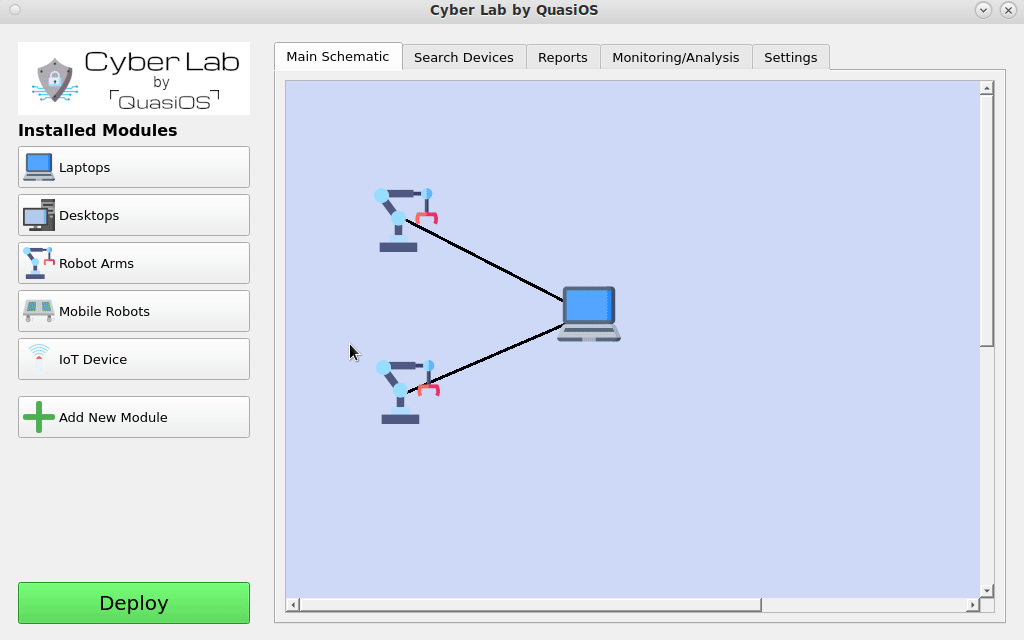
It is also possible to develop specialized interfaces for custom applications. This could for example be an app on a tablet in the production hall which only has two buttons; start and stop.
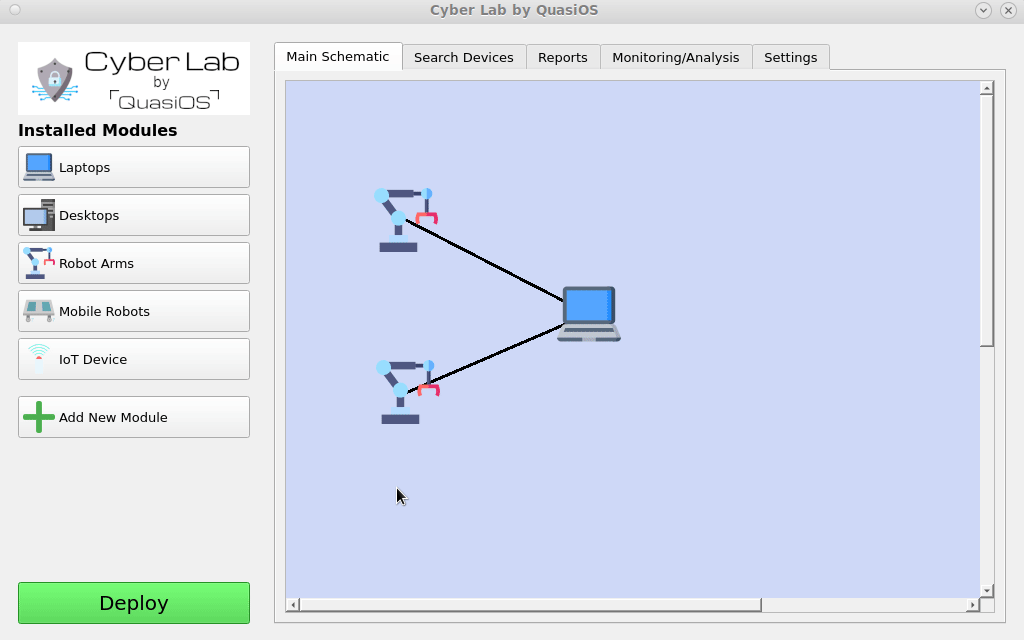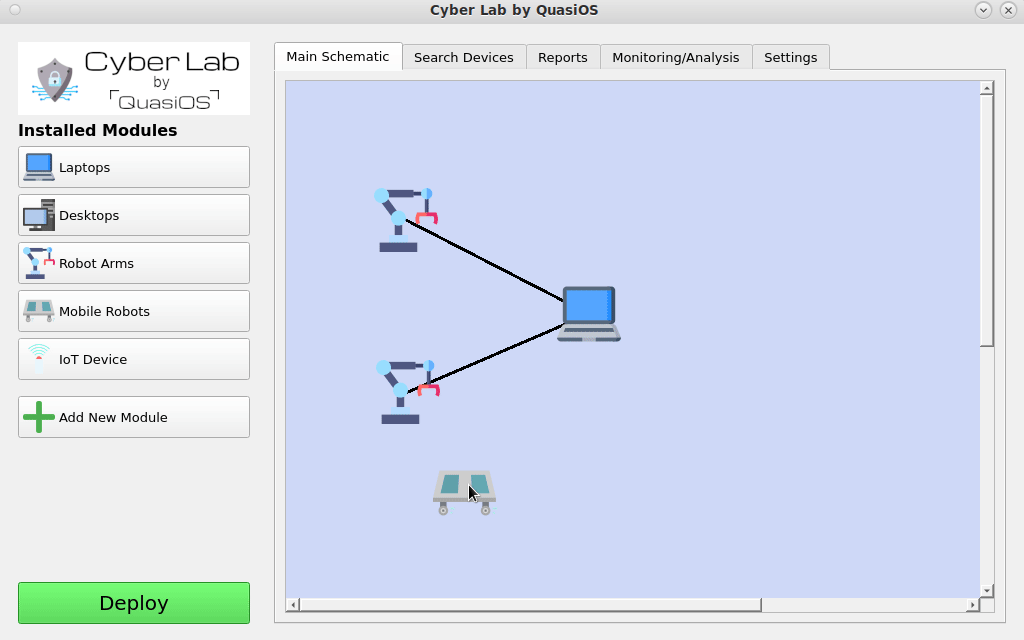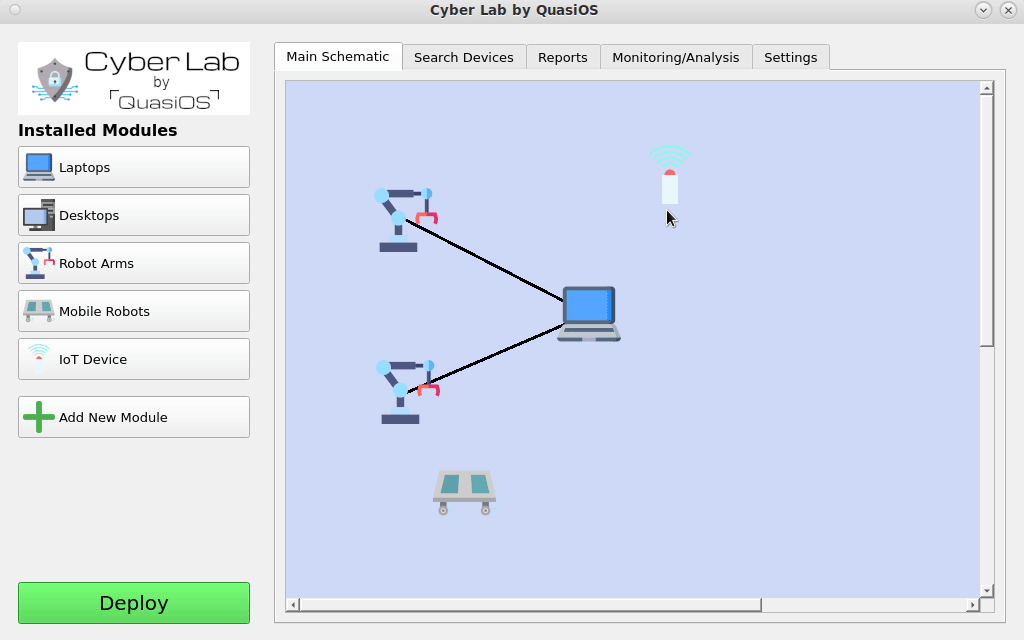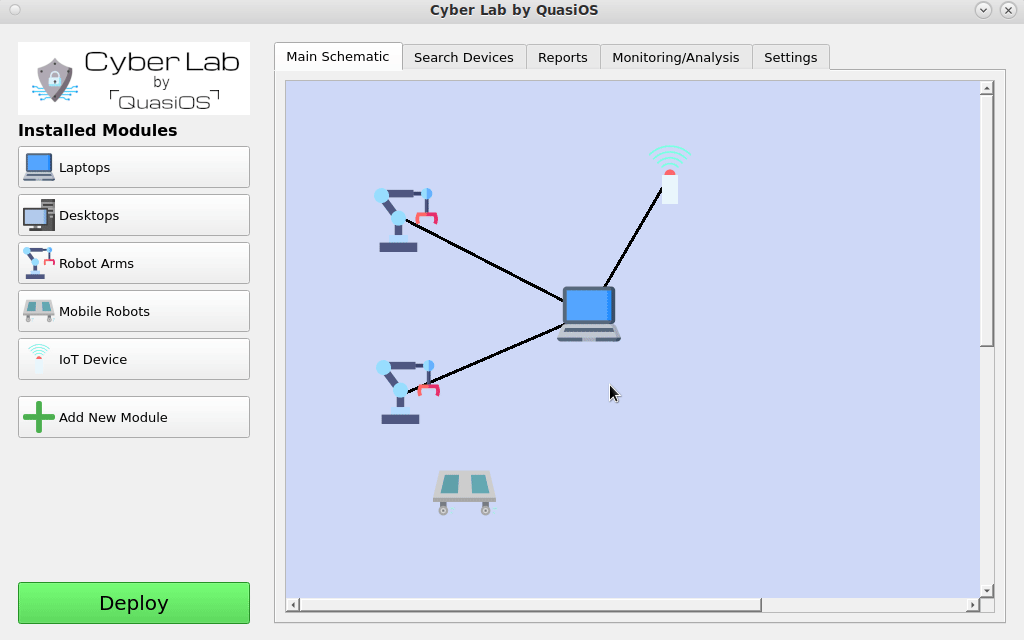
Modules for Anything
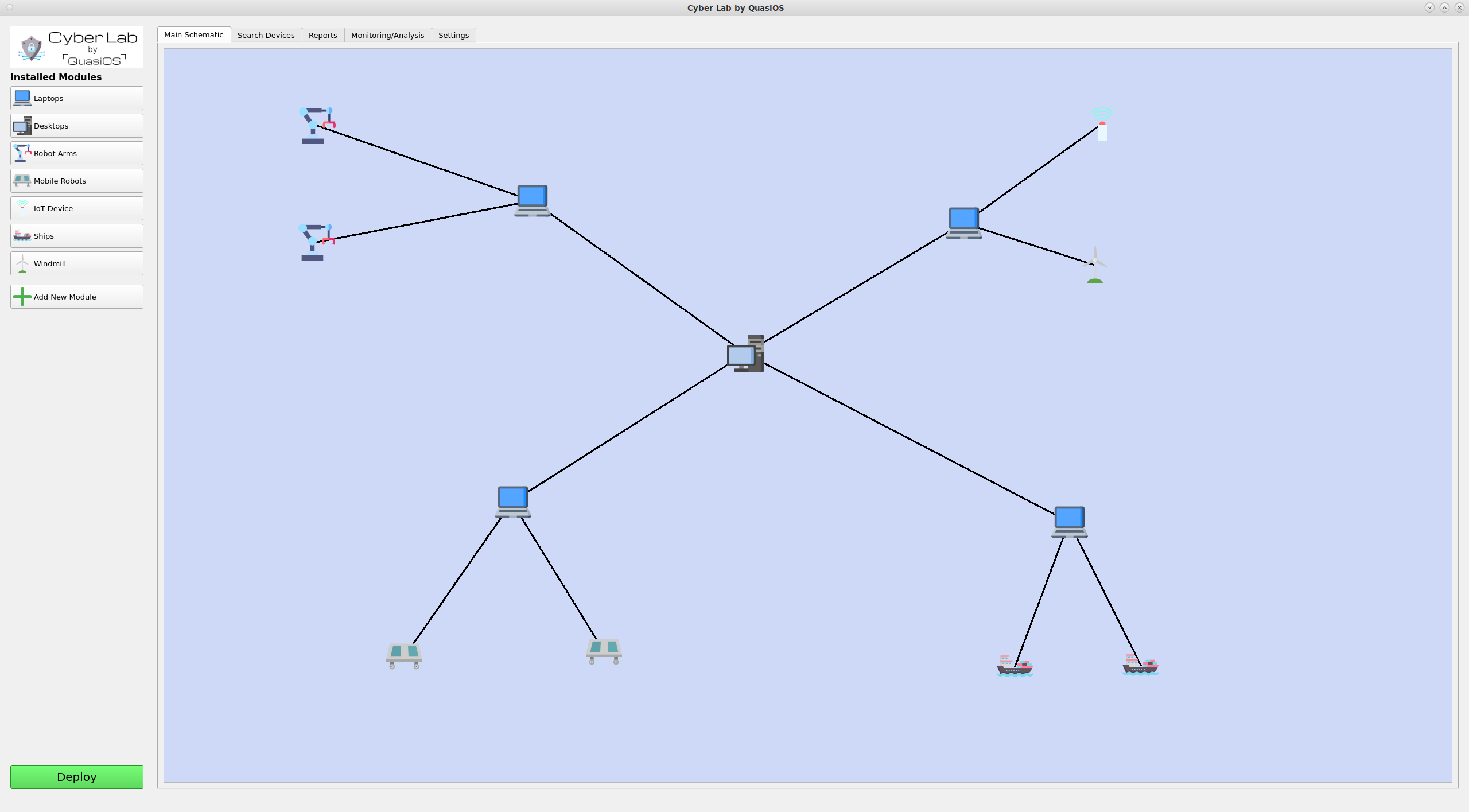
There can essentially be modules for anything. From Robots to IoT devices or even from ships to Windmills.
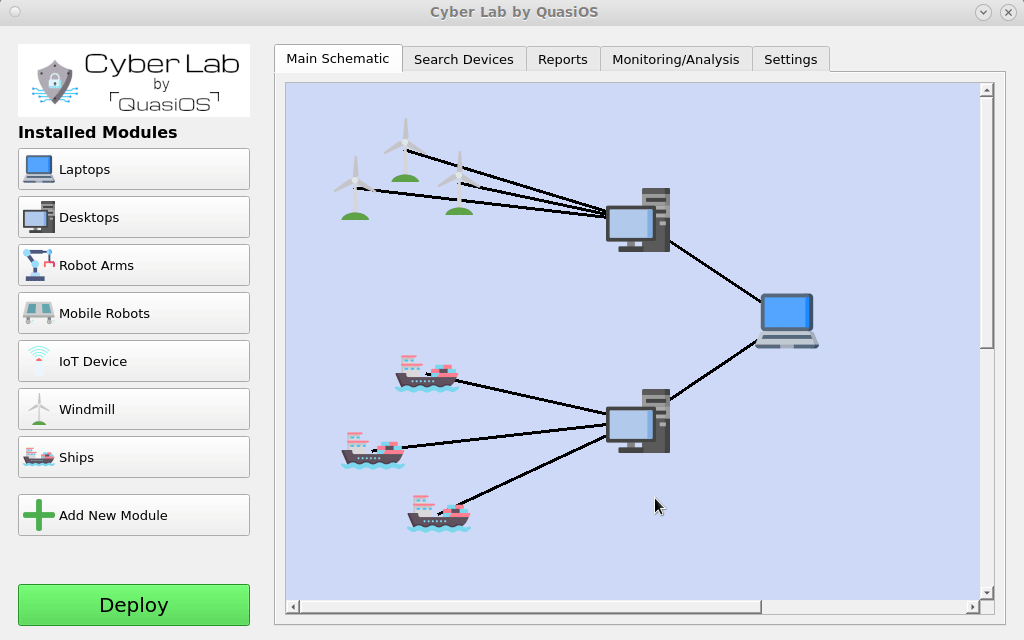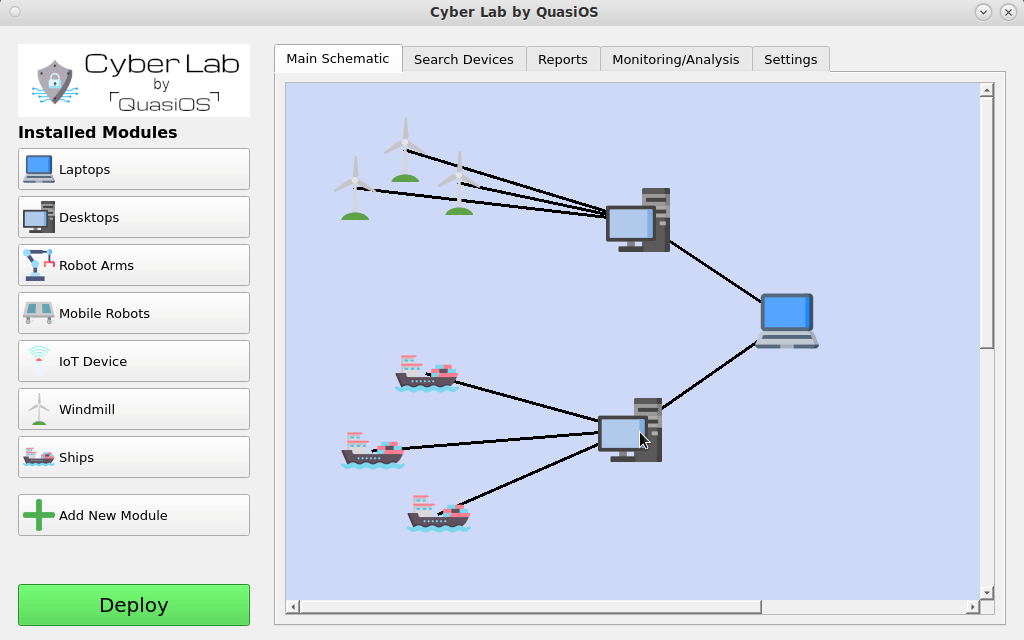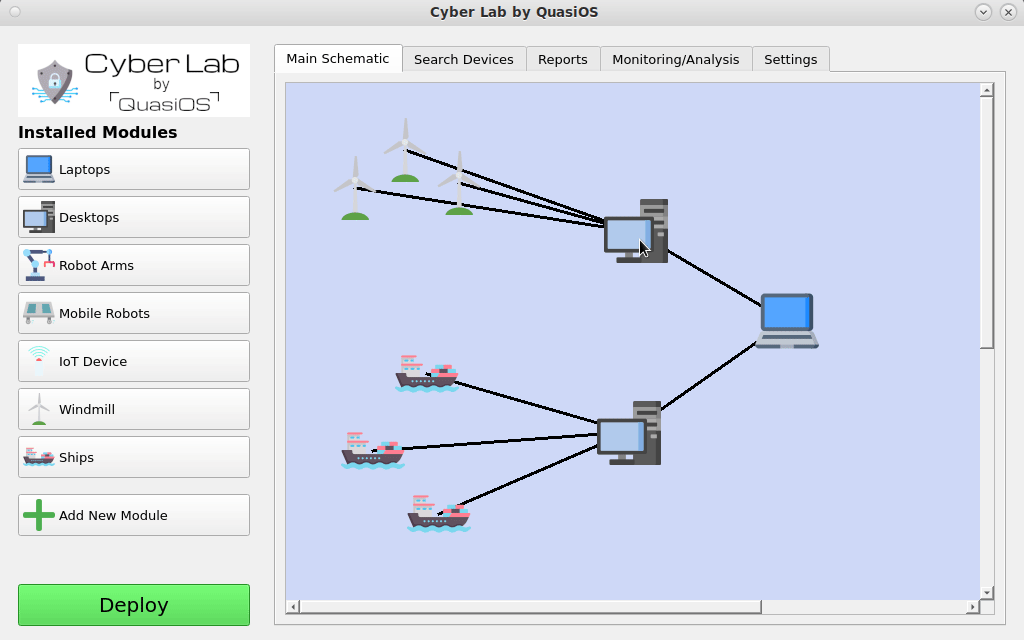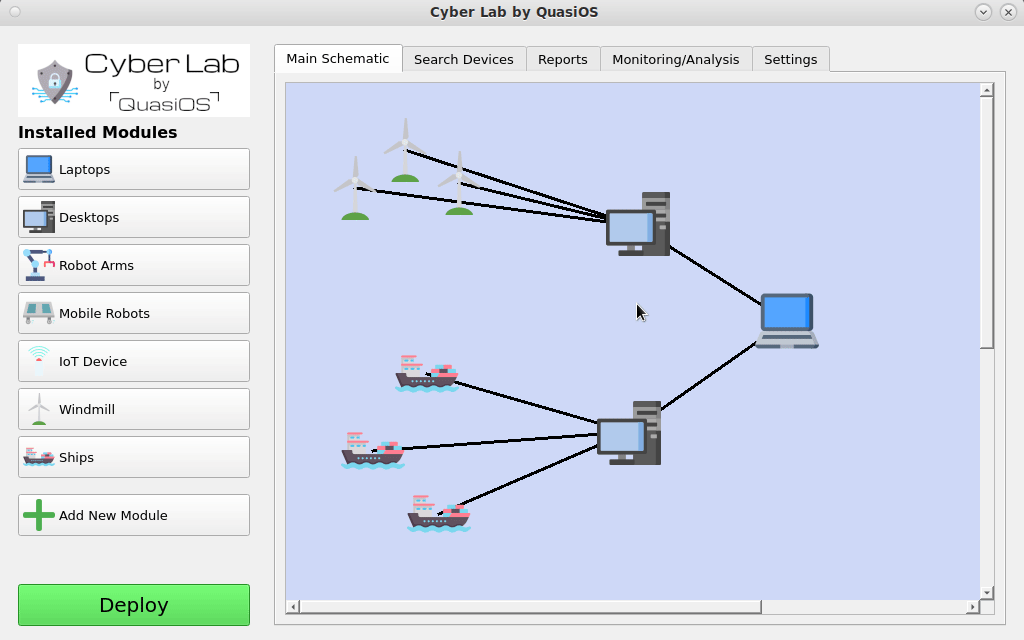
We imagine that most networked devices will have some common used operations, like monitoring or software updates. With vendor specific modules, it will be very easy to integrate them in Cyber Lab.
Expand the network
The network can be expanded to include more complex and also physical remote facilities. Even the entire organization could be designed.
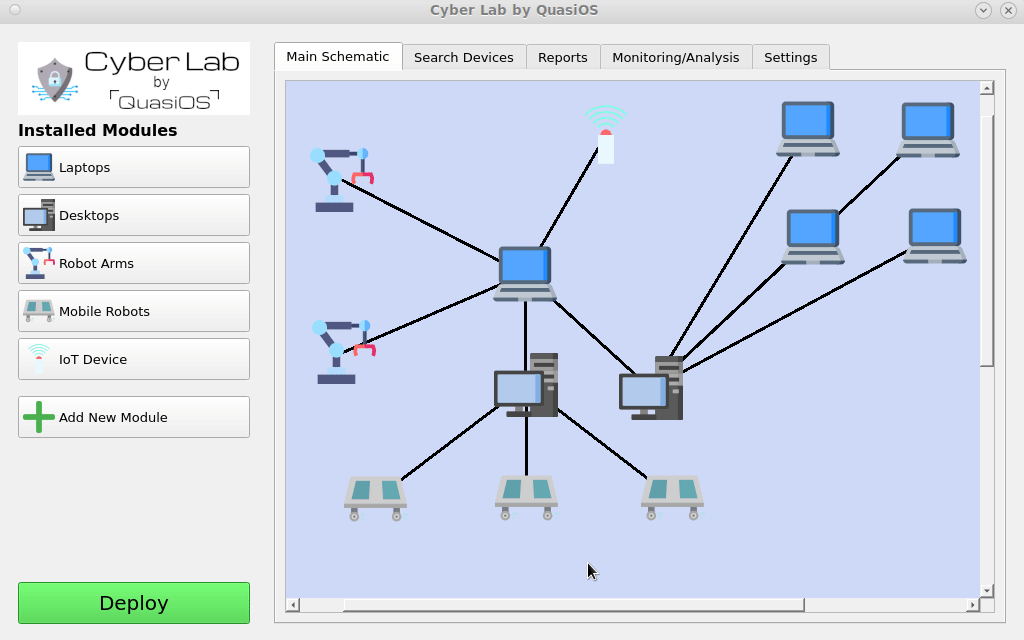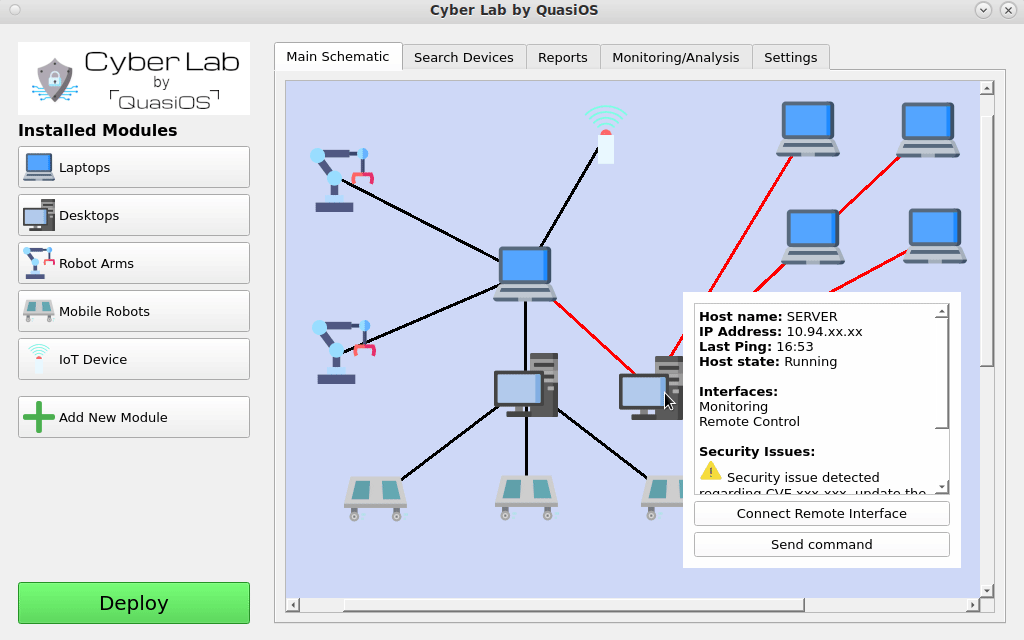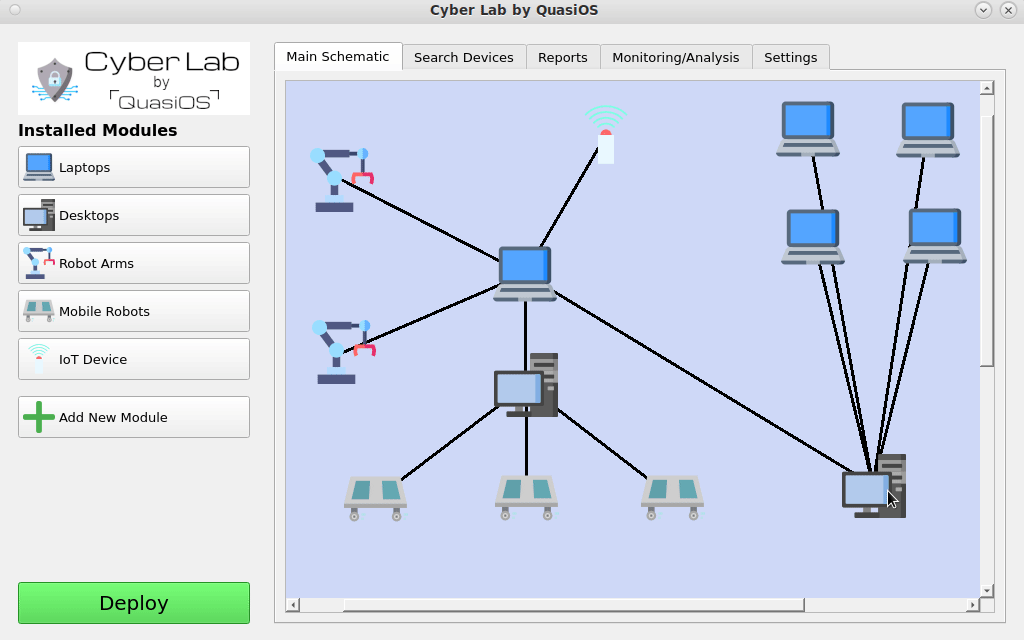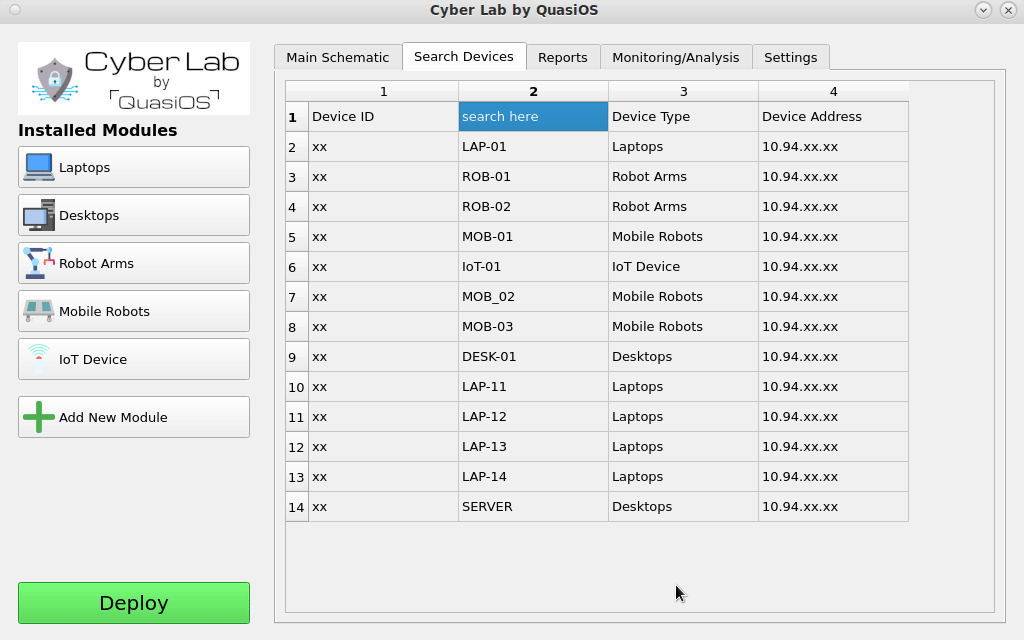
Setting up the system in Cyber Lab, Cyber Lab will keep track of which devices have the capability to send commands to other devices. It will handle and generate all needed cryptographic keys, and you will have the entire overview of the configuration.
Virtual Office
Cyber Lab can be used to visualize virtual offices. Lots of work is done remote and on laptops, and for a large organization it can be hard to locate and administrate devices because they are not physically present at the office, or if the interior design of the office changes. With Cyber Lab it is possible with drawings and labels to virtually visualise departments in the organization independent of their physical location in the real world office.
However, sometimes it is hard to physically locate servers and devices in a building, and Cyber Lab could facilitate actual floor plans or 3D rendering of buildings, such that it is possible to locate a device physically.
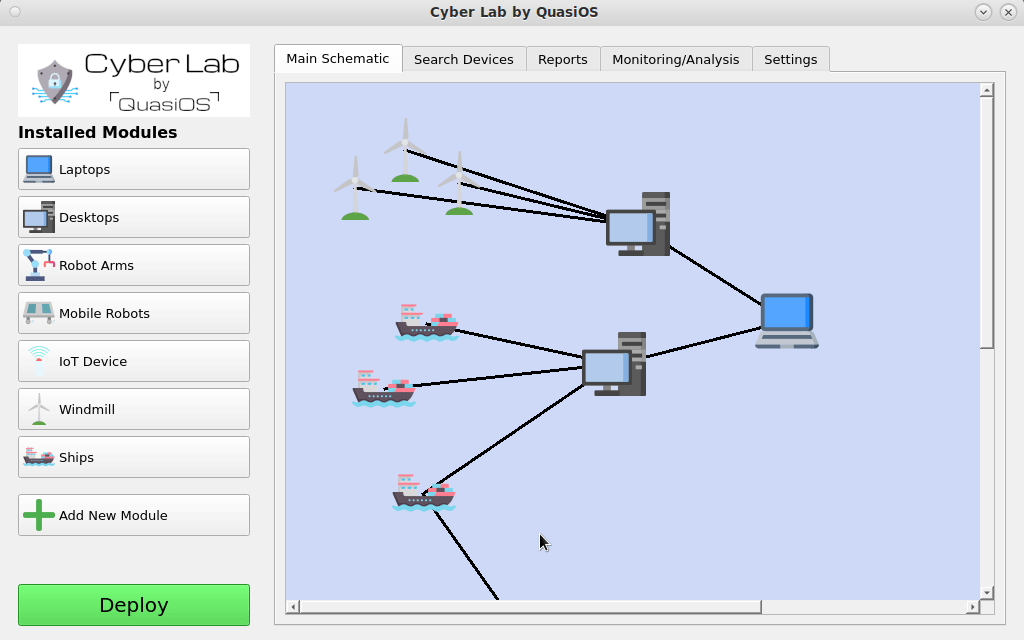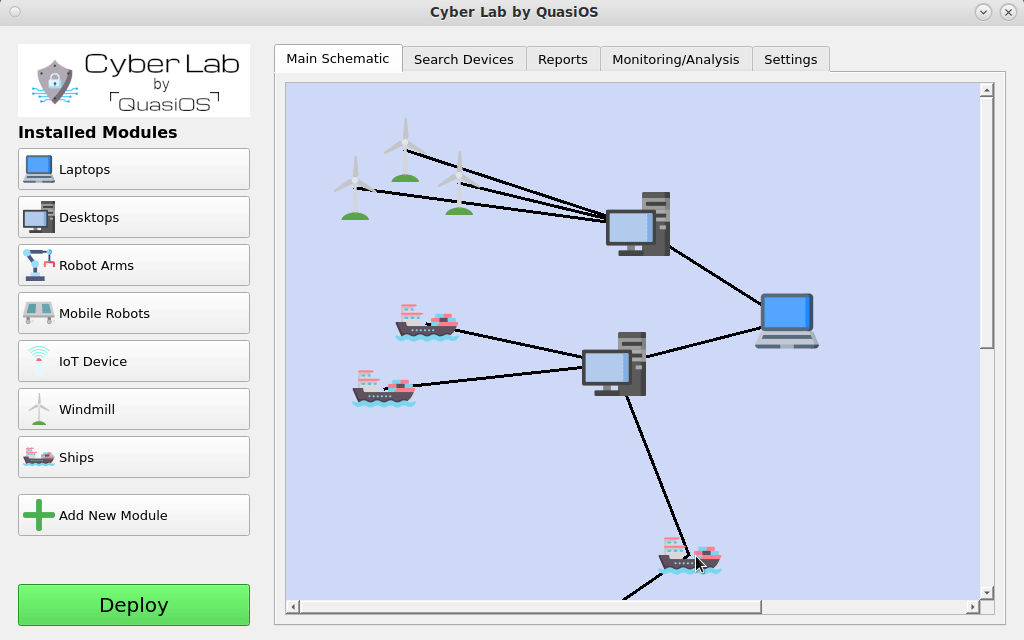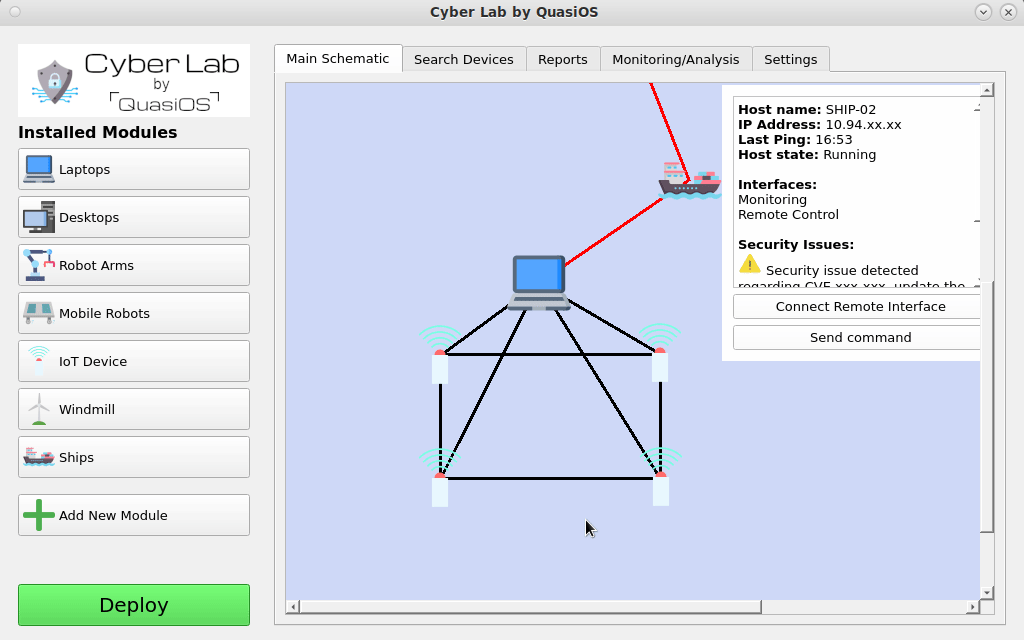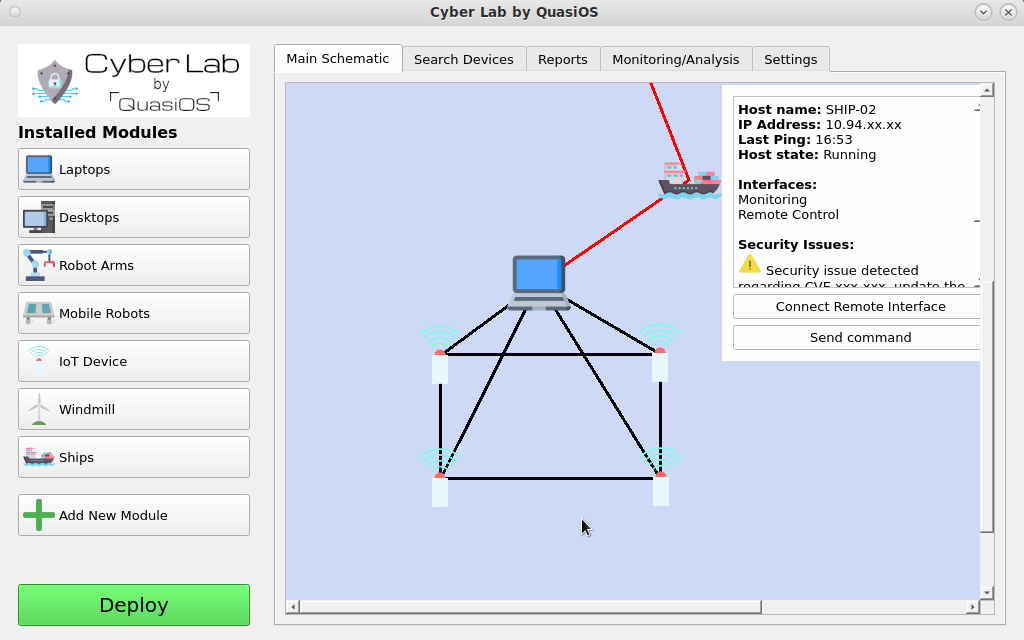
There could also be submaps inside the overall organization network. For example an organization with ships. From the shore we mostly think about the ships as one unit, but on the ships there are lots of devices and sensors. In Cyber Lab it will be possible to click on the ship and "zoom-in" to see the network map on the specific ship itself.
This is partly illustrated by this video, but the subnetwork should be a completely new schematic for the ship only.
Beta-Plus Development Programme
We are currently looking for firstmovers for our platform, helping us develop the best tool for everyone.We are looking for vendors with the hardware used in production facilities, e.g. Robot Arms, Mobile Robots, Drones, IoT devices etc. In the Beta-Plus Development programme we will collaborate in developing off-the-shelf modules for your specific devices and make the modules ready for sale.
As a facility owner in the Beta-Plus Development Programme you will get free access to Cyber Lab and the modules needed to design your production facility. We will assist you in the first time configuration of the environment, get you going and follow until everything works to your satisfaction.
Get in touch
Please send a mail to team@quasios.com to sign up for the Beta-Plus Development Programme* or to get the details about the showcase event.*We will only enroll a limited number for our Beta-Plus Development programme.
